Cyber Security protection
Managed for your business.
BlueReef Technology is a promise. A promise to treat your business like our own.
Protecting your business from data theft or damage is always going to be forefront in everything we do.

Why is Cyber Security for small businesses important?
At a base level, Cyber Security is the defence of Computers (including Laptops, mobiles, and tablets), Servers, Networks, Data, and Software from malicious attack or compromise. Some of the items that can be a factor to or at risk to cyber security threats include:
- Network Security
- Application Security
- Data Security
- Disaster Recovery
- Email Protection
- End users (Education).
Read more in our guide: The definitive guide to Cyber Security for SMEs
What are the Cyber Security Threats for SME?
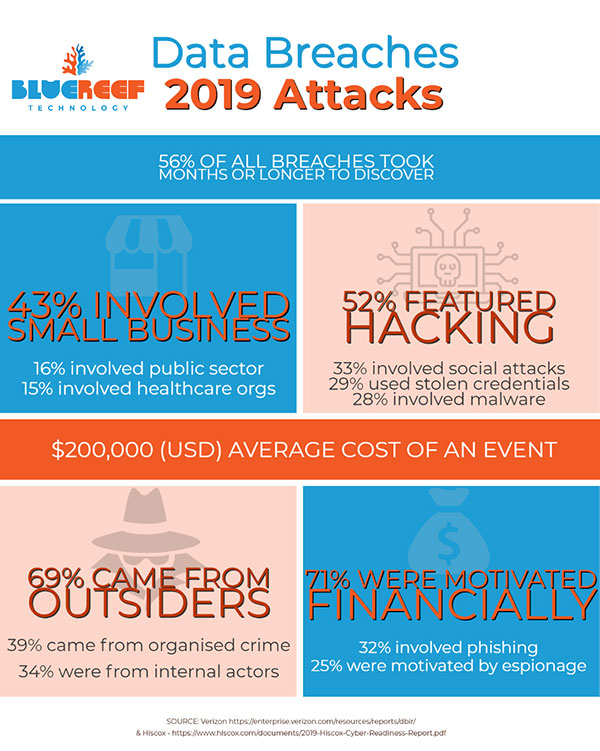
The IT Security threats to small business is very high compared to all other types. In 2019 a report by Verizon (2019 Data Breach Investigations Report), reported the victims of data breaches were broken down by:
- 43% involved Small Business
- 16% were breaches of public sector entities
- 15% involved healthcare organisations
- 10% were breaches of the financial industry.
How breaches occurred was also of concern:
- 52% of breaches featured hacking
- 33% included social attacks
- 28% involved malware
- 21% were caused by human error
- 15% were misuse by authorised persons
- 4% were physical breaches (physically stolen or accessed hardware).
The majority of attacks (69%) were instigated by external perpetrators, with 34% involving internal actors.
Unsurprisingly, 71% of all these breaches were financially motivated.
Of greatest concern however is that 56% of all breaches took months or longer to discover, and the average cost to business (of all sizes) was $200,000 USD, according to Hiscox (Cyber Readiness Report 2019).
The overwhelming takeaway is that cyber attacks are a very real and present danger to small business.

How can Cyber Security solutions work to protect your business?
Cyber Security Solutions should not be a 'cookie cutter' product. Every business should have a full audit and analysis of what is needed to properly secure their IT platforms.
We have a range of products, and services designed to mitigate cyber threats to your business - which we use to create a fit-for-purpose solution for our clients.
- Mail Protection: tools that scan inbound emails for spam, viruses & more before they even reach your mail server (Office 365, Exchange, Gmail or other). This tool is designed to be adaptive, and uses multiple virus engines to provide protection.
- Enhanced Mail Protection: All of the features above plus advanced tools to protect from phishing and other social attacks. Inbuilt spam tools have also been further enhanced.
- Mail Archive: Securely store emails for up to 10 years for each mailbox, independently from your mail server. With advanced search and encryption features, this tool copies email as they are sent and received from your email service directly.
- Agent Antivirus: Our agents antivirus - installed on all computers - has enterprise-grade virus engines running which are updated every three hours via our remote console. Viruses or other issues are reported directly to the helpdesk, allowing immediate response to any major threat.
- Agent Web Protection: The Agents include a Web Protection module - installed on all computers - which filters any website content downloaded to end users' computers. This can be filtered by multiple types of content (i.e. no staff can access social websites during business hours), and helps protect from malicious code.
- Network Security: Security gateways for local networks in business, with remote servicing to the helpdesk. These devices actively block attacks to a network, keep an eye on cyber threats and monitor activity to a device level.
- Cloud Desktop: The Cloud Desktop has advanced firewalls, enterprise-grade antivirus, backups and everything any firm could need to protect their data.
- Office 365: Correctly configured and maintained, Office 365 can be secured with tools like two factor authentication (2FA), dedicated admins, and disabling features (like auto-forwarding, etc.)
- And more...: We have a lot of tools and services designed to protect our clients. Each are brought in to any cyber security solution whenever needed.




08 8922 0000